We came across this recent Joint Cybersecurity Advisory paper: “Threat Actor Leverages Compromised Account of Former Employee to Access State Government Organization,” co-authored by the Cybersecurity & Infrastructure Security Agency (CISA) and the Multi-State Information Sharing & Analysis Center (MS-ISAC). The topic strikes a familiar chord, yet we both appreciate the thorough analysis provided by the authors to educate cybersecurity professionals on the details and mitigating factors. In our view, sharing real life experiences helps get the message across more impactfully than discussing abstract threat models and hypothetical attacks.
It makes you think … Do you know how quickly your organization responds to an employee or contractor leaving the organization? How unified are your HR and IT functions? Is your identity and access management (IAM) solution fit for the 21st century? With social engineering attacks such as phishing and man in the middle (MiTM) getting more sophisticated, do you have the tools in place to protect against them?
Let’s first look at the method used by the hacker described in this advisory paper and see what lessons we can learn from this attack.
Unidentified Threat Actor
The hack started with a government agency being alerted to a U.S. government employee’s credentials, host, and user information being offered for sale on the dark web. The incident response assessment determined that “an unidentified threat actor compromised network administrator credentials through the account of a former employee … to successfully authenticate to an internal virtual private network (VPN) access point … .”
The hacker then moved onto targeting the ex-employee’s on-prem environment, running several lightweight directory access protocol (LDAP) queries, and then moving laterally into their Azure environment.
The good news is the hacker didn’t appear to have progressed much further, presumably satisfied they had valid credentials that they could sell to other hackers to continue their nefarious acts.
The advisory paper references the MITRE ATT&CK® framework, which we’ve illustrated below.
These are the steps a threat actor would typically follow as they carry out an attack – starting at the 12 o’clock position (Reconnaissance), moving clockwise to Resource Development all the way to Impact.
NOTE: For more details about the typical stages of an attack and a comprehensive database of real threats used by adversaries, visit attack.mitre.org.
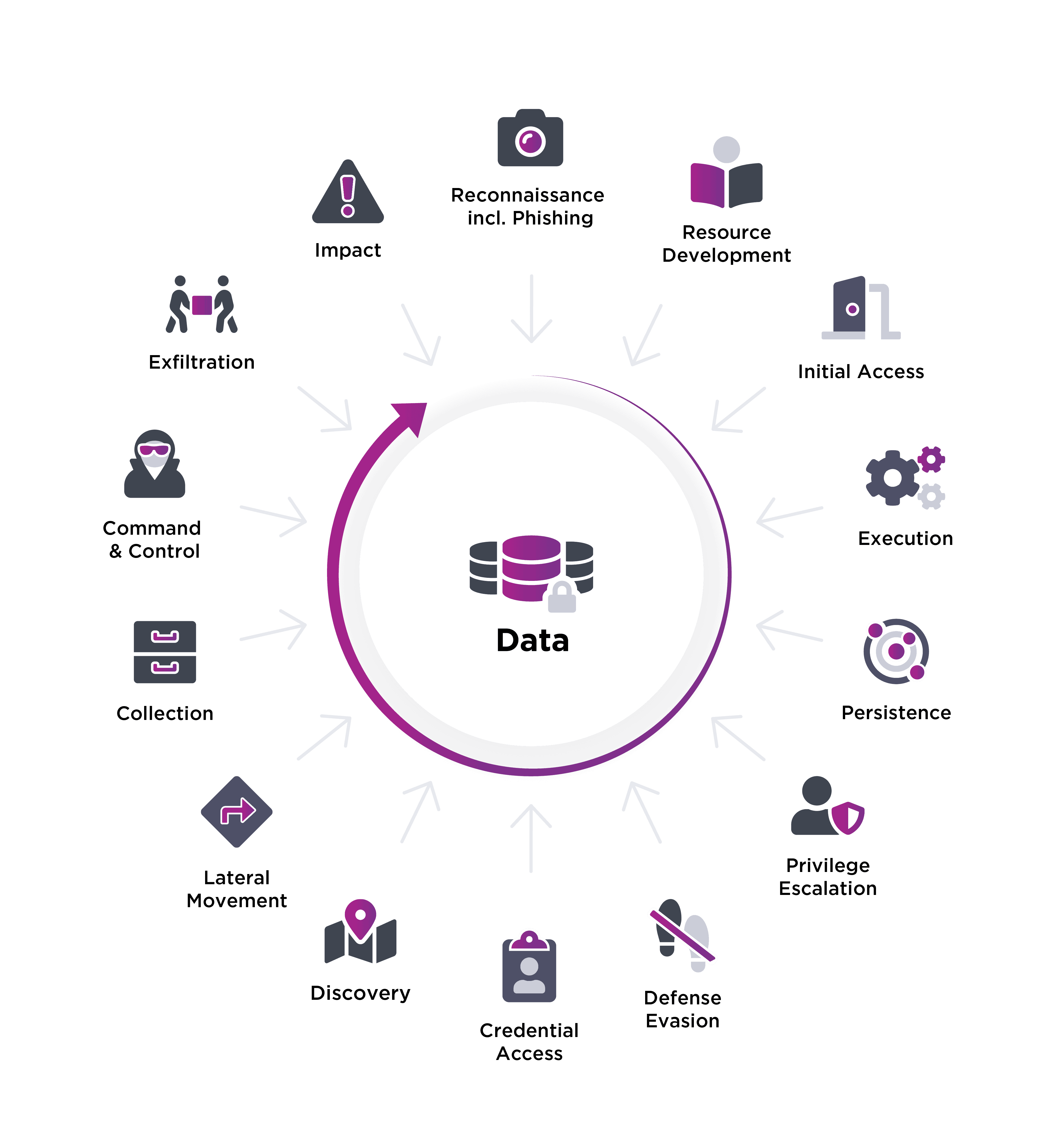
Figure 1: MITRE ATT&CK illustration of the threat actor’s modus operandi
USER1, referenced in the paper, likely followed these steps in sourcing the former employee’s credentials and then used them to access the network. Once on the network, they were able to locate a second set of credentials, labeled USER2. The advisory paper charts the progress of USER1 and USER2 through these stages as far as the Collection stage, where “the actor obtained USER2 account credentials from the virtualized SharePoint server managed by USER1.” As we mentioned, progress seems to have stalled and the paper states: “Analysis determined the threat actor did not move laterally from the compromised on-premises network to the Azure environment and did not compromise sensitive systems.”
Mitigations
What’s clear from the report is several simple errors facilitated this hack. Below, we’ve added some best practices to the MITRE ATT&CK illustration to show how to mitigate those errors.
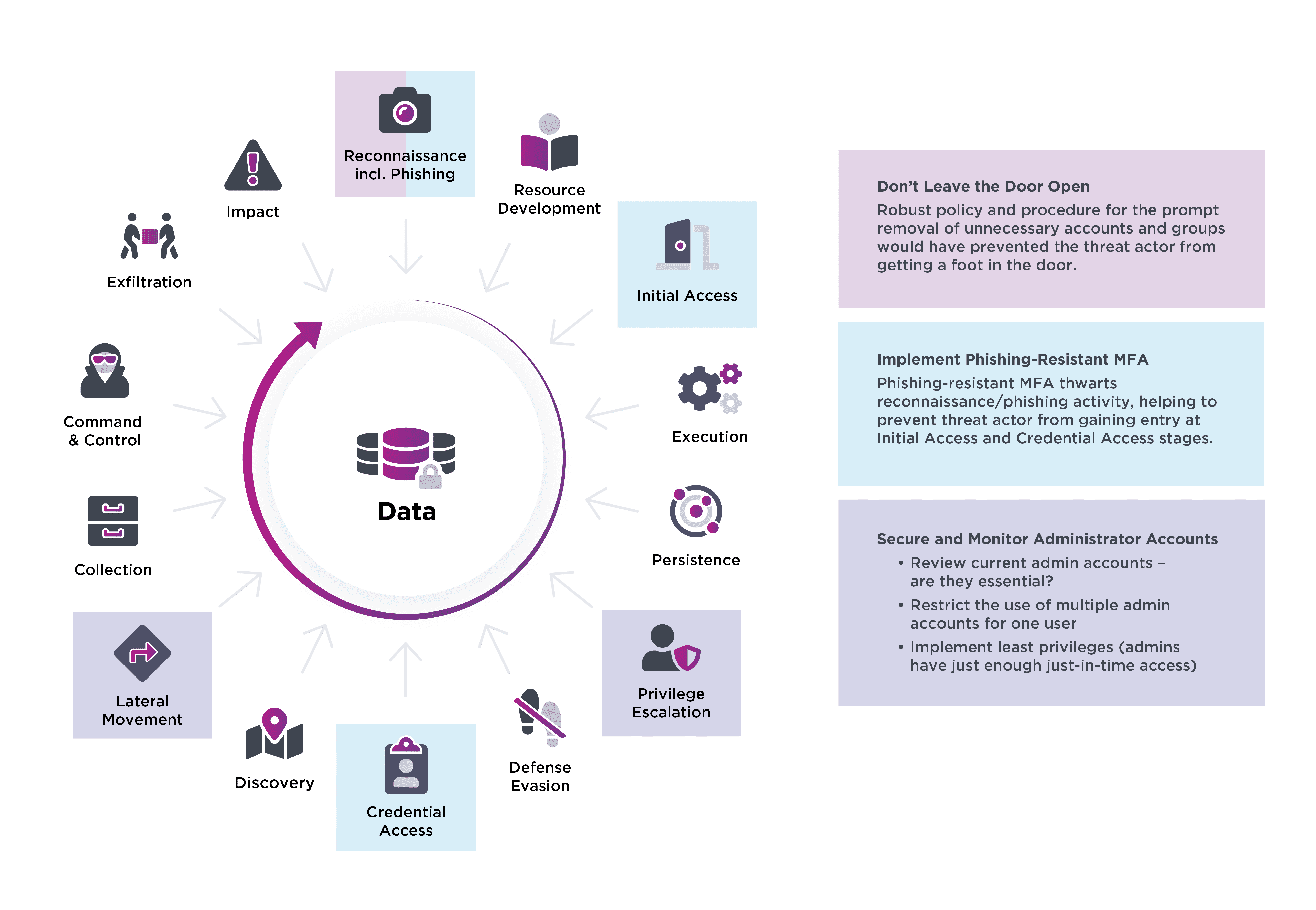
The joint Cybersecurity Advisory paper is a reminder of how threat actors are poised and ready to exploit weaknesses in an organization’s security posture. Some straightforward security measures would’ve halted this attack before it had even started. However, we know that threat actors are evolving and implementing more sophisticated attacks. Organizations might not always leave the door open, but they might not have secured the latch and attached the door chain to bolster their security posture.
We Can Help You Lock the Door
Entrust offers a comprehensive portfolio of solutions that not only would have helped the organization that was the victim in this particular situation, but can also help other organizations protect against more sophisticated attacks being used by threat actors.
KeyControl manages keys, secrets, and certificates – including credentials. KeyControl proactively enforces security policies by whitelisting approved users and actions while also recording privileged user activity across virtual, cloud, and physical environments – creating a granular, immutable audit trial of those accessing the system.
Entrust CloudControl improves virtual infrastructure security and risk management with features such as role-based access control (RBAC), attribute-based access control (ABAC), and secondary approval (two-person rule). These are important, especially when overseeing virtualized environments on a large scale with a team of busy system administrators. CloudControl provides the necessary guardrails and control measures to ensure that your system admin team consistently applies policies across your VM estate while also mitigating against inadvertent misconfigurations.
Entrust Phishing-Resistant MFA delivers precisely as advertised. Identity continues to be the largest attack vector, with compromised credentials and phishing being the leading causes of breaches. The traditional password adds to the poor user experience and is easily compromised. Even conventional MFA methods such as SMS one-time password (OTP) and push authentication are easily bypassed by attackers.
Credential Management and Access Trends
When examining credential management and access, there are prominent trends in identity and IAM that are receiving significant attention in the office of the CEO and the boardroom.
One prominent trend is the increasing adoption of phishing-resistant passwordless adaptive biometrics authentication. This helps prevent fraud and secure high-value transactions with risk inputs that assess behavioral biometrics and look for indicators of compromise (IOCs) based on various threat intelligence feeds.
Another trend is using identity proofing to enhance security layers, seamless onboarding processes, and the integration of digital signing to provide a unified digital identity experience. Many companies are grappling with the complexities of managing multiple identity providers (IDPs) and associated processes, as well as challenges related to MFA fatigue and phishing attacks targeting OTPs via SMS or email – particularly through adversary in the middle (AiTM) attacks.
Then there’s the management of diverse cybersecurity platforms – including various IDPs, MFA solutions, identity proofing tools, and standalone digital signing platforms – that can lead to productivity bottlenecks and costly administration overheads. Employing certificate-based authentication, biometrics, and other passwordless authentication methods – combined with identity proofing and digital signing within an integrated identity solution – helps streamline operations, reduce costs, and enhance user adoption. Plus, it also helps mitigate potential vulnerabilities associated with disjointed platform connections across enterprise IT environments. It’s a lot for organizations to take on board.
Entrust phishing-resistant identity solutions provide a complete identity and access management platform and comprehensive certificate lifecycle management capabilities to help you implement high-assurance certificate-based authentication for your users and devices.
Lessons Learned
Whether your organization is on a Zero Trust journey or just looking to strengthen your security posture, the attack discussed in the Joint Cybersecurity Advisory paper that started this conversation is a reminder that the threats out there are real – and organizations need to have robust security processes and procedures in place to keep that door firmly closed.
Learn more about Entrust solutions for strong identities, protected data, and secure payments.




